
How do we determine these are the unresolved APIs? Try using OllyDbg, find the OEP, it is fairly easy to find it if the sample was packed by UPX ;) , and Follow in Dump -> Memory Address to any API's call, for example:

Now in the Memory Dump window, switch to Address view and then you can see the list of APIs:


These are the IAT that we missed just now when loading it to IDA. So the next thing is to recover this so that we can continue static analysis on IDA. Scroll up until 0 byte memory address which is beginning IAT relative virtual Address (491cc) and scroll down until 0 byte memory address which is the ending IAT relative virtual address (49338).
Dump the sample using OllyDump, then we can start ImpREC to recover the IAT using the starting RVA we found just now. Using the AutoSearch button will give us:

Notice that the original IAT RVA found at 49284 seems to be incorrect. If you fix the dump with this option you will see the unresolved APIs as shown in the first figure. So we need to set the OEP, RVA and Size (49338-491cc) manually and select Get Imports:
 We can now fix the dump using Fix Dump button, select the file that was dumped by OllDbg just now. Done! Next we can load to IDA and see the result:
We can now fix the dump using Fix Dump button, select the file that was dumped by OllDbg just now. Done! Next we can load to IDA and see the result: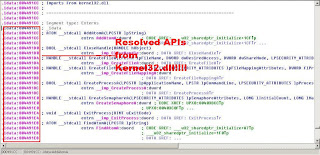
Signing off
~x9090